-
admin@dominant-it.com
-
(702) 514-0583
Penetration Testing
Identify Vulnerabilities and Strengthen Your Security Posture
In an increasingly connected world, businesses must stay one step ahead of cybercriminals to protect their valuable assets and sensitive data. Dominant-IT offers comprehensive penetration testing services to help you identify vulnerabilities in your IT infrastructure, prioritize risks, and strengthen your security posture. Our team of skilled cybersecurity professionals uses the latest techniques and tools to simulate real-world attacks, providing you with actionable insights and recommendations to enhance your defenses.
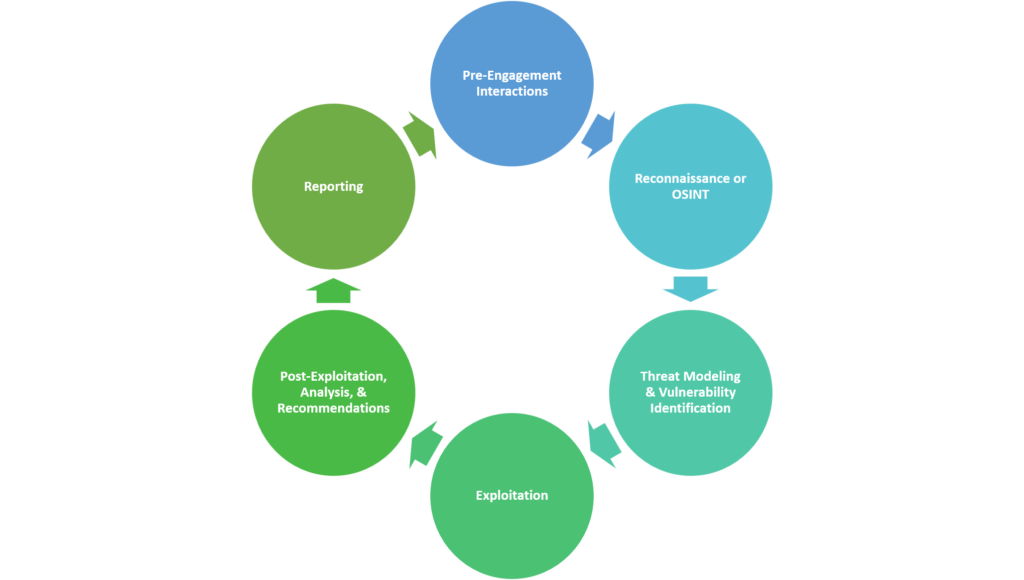
Our Penetration Testing Process:
- Pre-Engagement and Scoping: Our team works closely with you to understand your business objectives, IT environment, and security concerns. We then define the scope of the penetration test, including the systems, applications, and networks to be assessed.
- Reconnaissance: We gather information about your IT infrastructure, including public-facing assets, potential vulnerabilities, and security configurations. This data helps us to develop a targeted testing strategy that maximizes effectiveness.
- Vulnerability Assessment: Our cybersecurity experts conduct a thorough vulnerability assessment, leveraging both automated tools and manual techniques to identify potential weaknesses in your systems, applications, and networks.
- Exploitation: During the exploitation phase, our team simulates real-world attacks to test your security measures and determine the impact of potential breaches. This hands-on approach enables us to uncover vulnerabilities that might be missed by automated scans.
- Reporting and Recommendations: Upon completion of the penetration test, we provide you with a detailed report that outlines our findings, including identified vulnerabilities, exploited systems, and potential risks. We also offer actionable recommendations for addressing these issues and enhancing your overall security posture.
- Re-Testing and Validation: As part of our commitment to your ongoing security, we offer re-testing and validation services to ensure that the implemented fixes are effective and that your IT environment remains secure.
Why Choose Dominant-IT for Penetration Testing?
- Expertise: Our team of certified cybersecurity professionals has extensive experience in conducting penetration tests across various industries and technologies.
- Customized Approach: We tailor our penetration testing services to your unique business needs, ensuring that our assessments are targeted, comprehensive, and effective.
- Proactive Security: Our proactive approach to cybersecurity enables you to identify and address vulnerabilities before they can be exploited by malicious actors.
- Comprehensive Reporting: We provide clear, actionable reports and recommendations to help you prioritize risks and make informed decisions about your security investments.
- Ongoing Support: We are committed to your long-term security, offering re-testing and validation services to ensure that your IT environment remains protected against evolving threats.
Contact Us:
Don’t wait for a security breach to expose your vulnerabilities. Contact Dominant-IT today to schedule a penetration test and discover how our expert team can help you fortify your defenses and protect your business from potential threats. Reach out to us for a free consultation and take the first step toward a more secure digital future.
Please contact us via phone (702) 514-0583 or our online contact form.
